Threat Model Diagram Example Abstract Forward Podcast #10: C
Threat threats itsm Threat modeling model example security diagram application threats agile will full simplified source following A guide to threat modelling for developers
Threat modeling explained: A process for anticipating cyber attacks
Website threat modeling Threat model stride diagram example sample template Stride threat model
Stride threat model
Process flow vs. data flow diagrams for threat modelingThreat modeling cyber process attack tree attacks diagram cso sa cc anticipating explained Abstract forward podcast #10: ciso risk management and threat modelingWhat is threat modeling? (+top threat model examples).
Threat modelling buildingAgile threat modeling How to get started with threat modeling, before you get hacked.Free threat modeling tool.
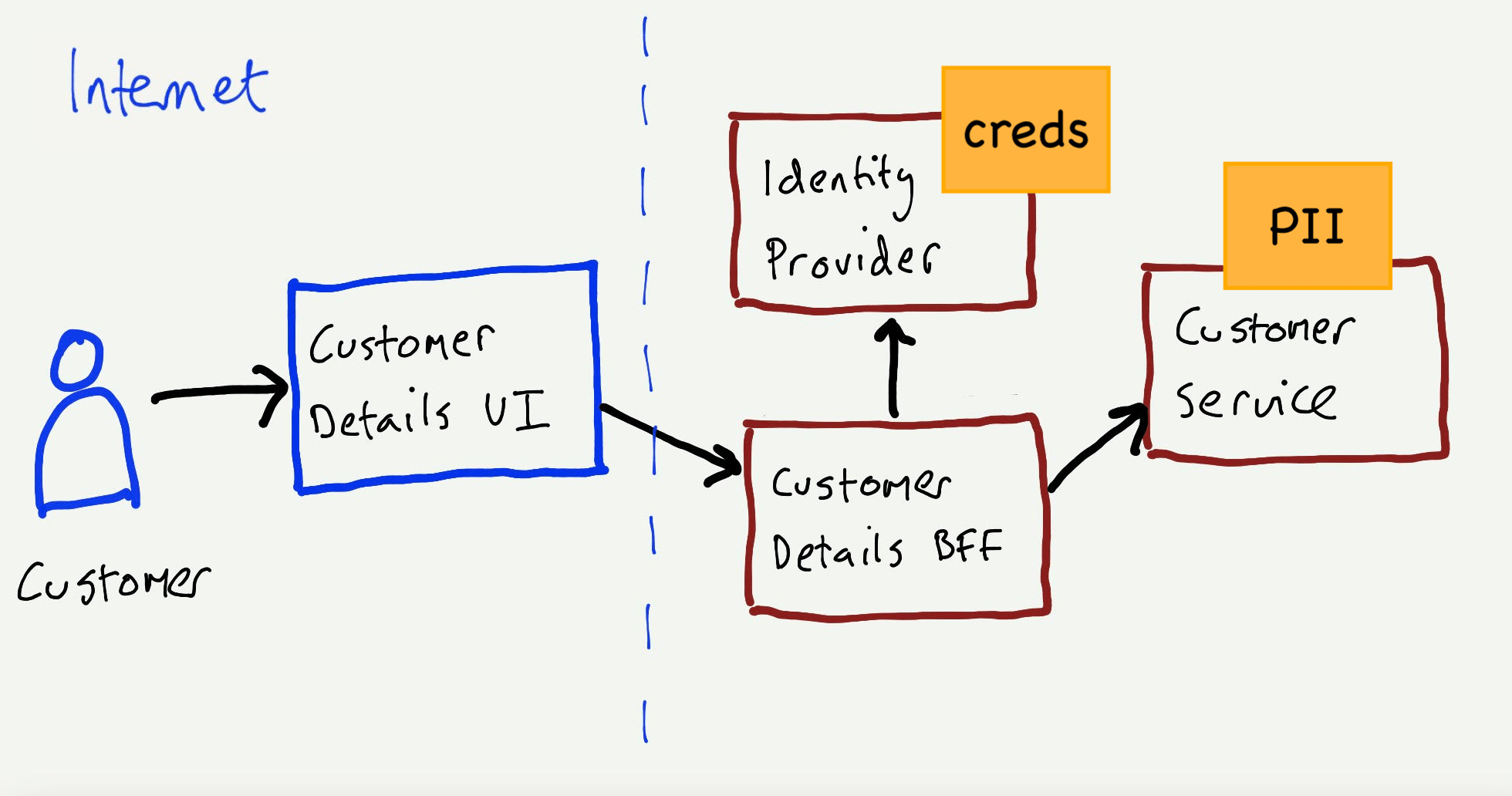
Stay safe out there: threat modeling for campaigners
Threat model templateThreat model diagram ecosystem thing map today part do crashspace cropped The threat model for the example.Threat modeling model example tool stride dfd microsoft diagram flow examples data security rbd ceph using mcp mirantis practices q4.
Threat model modeling system single example web entire just netmeisterThreat modeling explained: a process for anticipating cyber attacks What is threat modeling? definition, methods, exampleDiagram threat model stride online banking example modeling flow application data visual website templates template diagrams.
.png)
Threat risk assessments
Threat modeling processThreat modeling for beginners Know your enemyThreat model diagram.
Flow data diagrams process threat modeling diagram vs application dfd cloud engineering user owasp source response choose boardThreat model modeling batman campaigners mostly learned worrying stop love safe stay there lu tiffany mit might created courtesy look Threat modeling refer easily risks assign elements letter them number listing when may getWhat is threat modeling? 🔎 definition, methods, example (2022).

1: microsoft threat modeling tool -wfac architecture threat model
Threat modelingThreat dev Threat model am creating personal own answering diagram above questionsThreat example.
Website threat modelingThreat model template Stride bankingHow to perform systemic threat modelling — an example.

Threat model template
Threat modeling website model diagram template diagrams onlineMirantis documentation: example of threat modeling for ceph rbd Threat modeling for driversThreat tool modelling example stride paradigm.
Threat model playbookThreat model modeling examples top Creating your own personal threat modelSample threat model.

Threat modelling
Stride threat model template .
.






